
mortage applications processed by digital mortgage software provider, Blend (in 2018 alone).


Our team comes from an extensive banking background, so we know how tricky compliance can be. This is why our solution provides 100% compliance automation for all onboarding applications!

Thanks to modern encryption methods, all data provided by prospects remains secure and free from cyberthreats.
We also provide an extra layer of security through 2FA, in order to prevent any attempts of social hacking, the most common method of hacking nowadays


businesses and individuals lost through email fraud in 2020, more than any other type of cybercrime
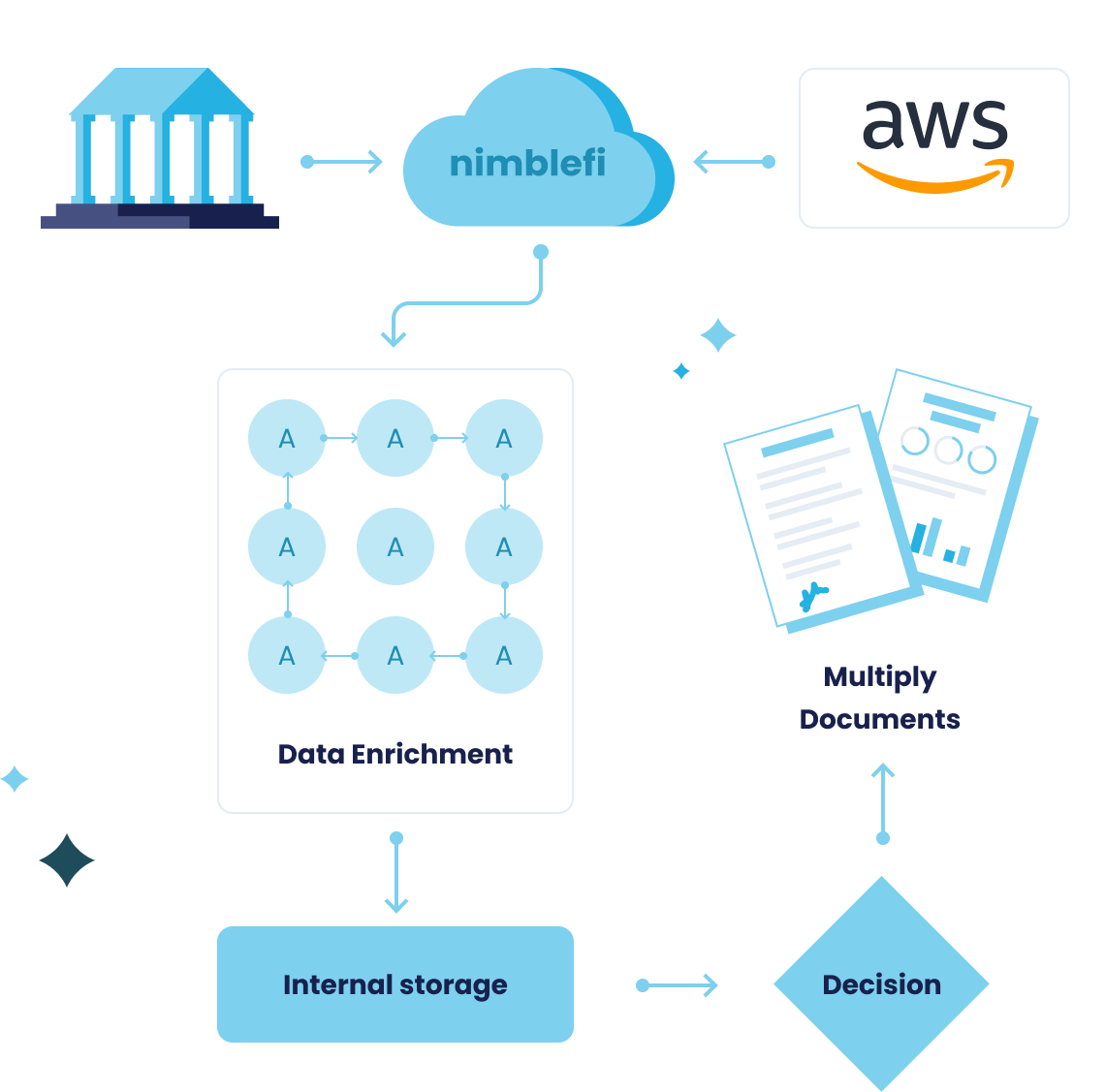
For as long as Nimblefi is operating on behalf of the financial institution, we provide the data integrity, data infrastructure, security and maintance for the data. This data is only accessible by the financial institution; this ensures complete privacy!
